Confidential. Controlled. Command-Ready.
Convay enables real-time collaboration for defense and law enforcement agencies with unmatched security and sovereignty.
Used by today’s top government agencies






Secure, Reliable, and Built for Command


Sovereign Data Control
Deploy Convay on national or private infrastructure so sensitive intelligence never leaves your control.


Granular Access Management
Assign roles, clearance levels, and permissions to maintain operational discipline and prevent unauthorized sharing.


Confidentiality Chain
Trace every shared file and message to its source, ensuring accountability in mission-critical communication.
Collaboration That Strengthens Command and Control
Confidential Briefings, Clear Decisions
Conduct encrypted briefings across units and field teams with verified access and real-time updates.
Secure Meeting Rooms
Host classified meetings with clearance-based access.
End-to-End Encryption
Keep mission data fully protected from interception.
Role-Based Permissions
Control visibility by rank and department.
AI Summaries
Generate accurate mission brief reports instantly.
Rapid Response When Every Second Counts
Coordinate between defence, police, and emergency units instantly during crises.
Instant Alerts
Broadcast emergency updates to all active teams.
Unified Command Dashboard
Oversee operations from a single control panel.
Offline Mode
Stay connected even in low-signal environments.
AI Transcription
Record decisions and create quick follow-up summaries.
Secure Information, Accountable Sharing
Exchange classified information with traceable access and built-in leak prevention.
Confidentiality Chain
Track who accessed and shared intelligence data.
Leak Tracking & Watermarking
Identify unauthorized disclosures instantly.
Audit Logs
Maintain a verifiable trail for every shared file.
Encrypted File Sharing
Protect sensitive documents in transit and at rest.
Preparedness Through Secure Training
Conduct virtual tactical training or simulations with attendance and performance tracking.
Attendance Tracking
Log every participant automatically.
Recording & Playback
Archive sessions for debrief and analysis.
AI Notes
Capture highlights and key learnings automatically.
Polling Tools
Evaluate readiness and gather quick responses.
Unified Coordination Across Forces
Connect multiple security agencies for real-time, multi-party operations.
Role-Based Access
Manage cross-agency visibility securely.
AI Translation & Subtitles
Overcome language barriers instantly.
Unified Communication
Chat, meet, and share files under one secure network.
Scheduling Tools
Plan joint operations with centralized oversight.
Every Operation, Fully Accountable
Record, document, and archive missions for audits or investigations.
Meeting Recording & Archiving
Preserve mission discussions securely.
AI Summaries
Generate structured mission debriefs.
Audit Trails
Ensure transparency and traceability in reporting.
Data Sovereignty Controls
Keep all mission data stored within national servers.
Advanced Features for Secure Operations
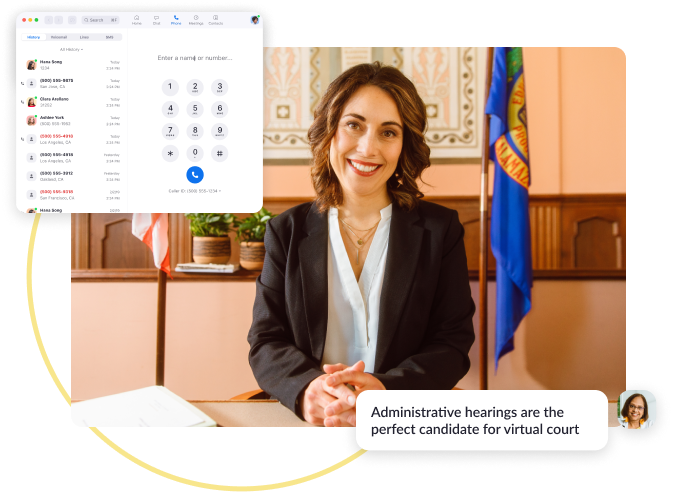
Secure Meeting Rooms
Create classified briefing rooms with limited access and instant termination controls for high-security sessions.
Leak Tracking & Watermarking
Detect, trace, and prevent unauthorized sharing of sensitive media or intelligence reports.
Granular Role Permissions
Define access by rank, department, or clearance level to ensure strict operational hierarchy.

Multi-Device Sync
Allow field agents, command centers, and mobile teams to coordinate seamlessly across devices.

Meeting Recording & Archiving
Record and store classified meetings for debriefings, post-operation analysis, and audits.

AI Transcription & Translation
Generate secure transcripts and real-time multilingual communication to enhance situational awareness in global or joint operations.
Frequently Asked Questions
-
How secure is Convay for classified communication?
Convay uses end-to-end encryption, on-premise deployment, and the Confidentiality Chain to ensure zero data exposure to external servers.
-
Can Convay operate in restricted or low-bandwidth environments?
Yes. Convay’s adaptive bitrate technology maintains connection even under limited network conditions.
-
How does Convay handle evidence or intelligence sharing?
Shared files are encrypted, watermark-protected, and tracked through immutable audit trails ensuring chain-of-custody integrity.
Try Convay & Experience the Future of Collaboration
White-label collaboration, tailored to your organization with
full control over data, features, and scale.




